Introduction to Cryptography & Cryptocurrencies
Securing Digital Assets
This topic provides a foundational understanding of the technologies behind cryptocurrencies.
 A. Cryptography: The Science of Secure Communication
A. Cryptography: The Science of Secure Communication
- What it is: Cryptography is the art and science of concealing information. It involves techniques for encrypting (scrambling) data so that it is unreadable to unauthorized parties and decrypting (unscrambling) data to make it readable again. It's the backbone of secure communication in the digital age.
-
Key Concepts:
- Encryption: The process of converting plain text into ciphertext (unreadable format).
- Decryption: The process of converting ciphertext back into plain text.
- Key: A secret value used in the encryption and decryption processes. The strength of the cryptography depends on the key.
- Algorithms: The mathematical formulas used for encryption and decryption.
-
Types of Cryptography Relevant to Cryptocurrencies:
-
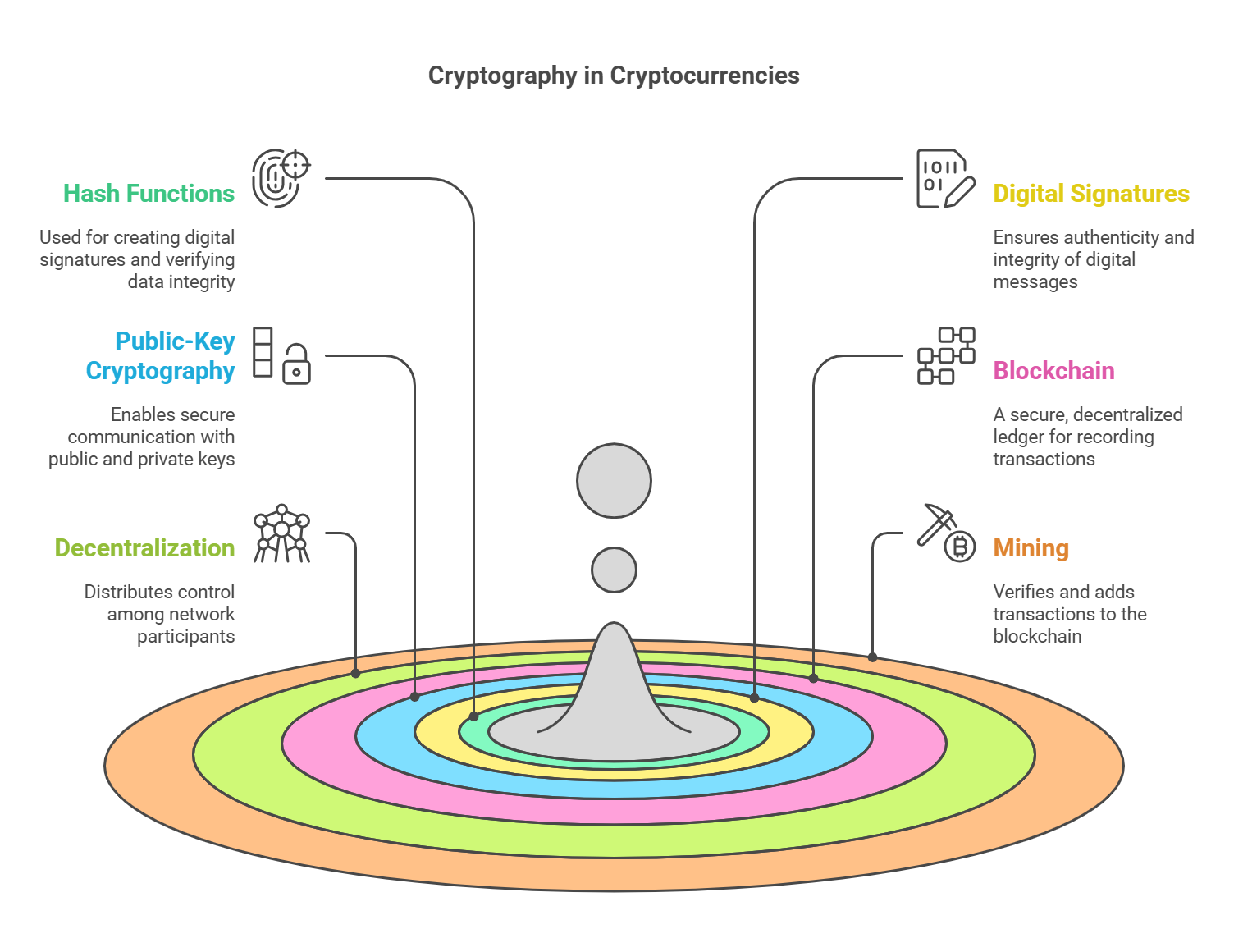
Hash Functions:
- What they are: One-way functions that take an input (data) and produce a fixed-size output (hash).
-
Key Properties:
- Deterministic: The same input always produces the same output.
- Preimage Resistance: It is computationally infeasible to find the input that produces a given hash.
- Collision Resistance: It is computationally infeasible to find two different inputs that produce the same hash.
- Examples: SHA-256 (used in Bitcoin), Keccak-256 (used in Ethereum).
- Use in Cryptocurrencies: Used for creating digital signatures, verifying data integrity, and creating Merkle trees (for efficient data summarization).
-
Digital Signatures:
- What they are: A way to verify the authenticity and integrity of a digital message (e.g., a transaction).
- How they work: The sender uses their private key to create a digital signature of the message. The receiver uses the sender's public key to verify the signature.
-
Key Properties:
- Authentication: Proves that the message came from the claimed sender.
- Integrity: Ensures that the message has not been altered since it was signed.
- Non-Repudiation: Prevents the sender from denying that they sent the message.
- Algorithms: Elliptic Curve Digital Signature Algorithm (ECDSA) is commonly used (Bitcoin, Ethereum).
-
Public-Key Cryptography (Asymmetric Cryptography):
- What it is: Uses a pair of keys: a public key (which can be shared with anyone) and a private key (which must be kept secret).
-
Key Properties:
- The public key can be used to encrypt messages that can only be decrypted with the corresponding private key.
- The private key can be used to create digital signatures that can be verified with the corresponding public key.
-
Hash Functions:
B. Cryptocurrencies: Digital Cash Secured by Cryptography
- What they are: Digital or virtual currencies that use cryptography for security. Cryptocurrencies are typically decentralized, meaning they are not controlled by a single entity (like a central bank).
-
Key Concepts:
- Blockchain: A distributed, immutable ledger that records all transactions. It is secured by cryptography and maintained by a network of computers. Each "block" contains a batch of transactions and a link to the previous block, forming a chain.
- Decentralization: No single entity controls the cryptocurrency network. Control is distributed among many participants.
- Mining: The process of verifying and adding new transactions to the blockchain. Miners solve complex cryptographic puzzles to earn newly created cryptocurrency (and transaction fees). (Note: Not all cryptocurrencies use mining; some use other consensus mechanisms like Proof of Stake).
- Wallet: A software program or hardware device that stores the user's private keys and allows them to send and receive cryptocurrency.
- Transaction: A transfer of cryptocurrency from one account to another, recorded on the blockchain.
- Consensus Mechanism: The method used to agree on the valid state of the blockchain (e.g., Proof of Work, Proof of Stake).
-
Key Properties:
- Decentralized: Not controlled by a central authority.
- Transparent: All transactions are recorded on a public ledger (the blockchain).
- Secure: Cryptography ensures the security and integrity of transactions.
- Limited Supply (Often): Many cryptocurrencies have a fixed supply, which can help to protect against inflation.
- Examples: Bitcoin (BTC), Ethereum (ETH), Litecoin (LTC), Ripple (XRP).
C. How Cryptography Enables Cryptocurrencies:
- Secure Transactions: Digital signatures ensure that only the owner of a cryptocurrency can spend it.
- Immutable Records: Hash functions link blocks together in the blockchain, making it extremely difficult to alter the transaction history.
- Decentralized Control: Public-key cryptography allows anyone to participate in the network without requiring permission from a central authority.
- Trustless System: Cryptography and blockchain technology enable a "trustless" system, where users don't need to trust each other or a central authority. The system is secured by mathematical proofs and code.

No Comments